Microsoft Bot Unvalidated File Upload: The security issue allows a malicious actor to upload any file without validating the extension or content type of the file.
Acknowledgment: Microsoft Online Service Acknowledgements for July 2019 (https://portal.msrc.microsoft.com/en-us/security-guidance/researcher-acknowledgments-online-services?rtc=1)About Microsoft Bot Framework: Azure Bot Service enables you to build intelligent, enterprise-grade bots with ownership and control of your data. Begin with a simple Q&A bot or build a sophisticated virtual assistant.
Use comprehensive open source SDK and tools to easily connect your bot to popular channels and devices. Give your bot the ability to speak, listen, and understand your users with native integration to Azure Cognitive Services.
URL
https://webchat.botframework.com/embed/TaxiLimeBot?s=xMHlV-9UR7c.cwA._H8.kLpVmFx6sOsqfBAKTic2_YqvcPsy5N8XBXT5a4h4jio
https://webchat.botframework.com/embed/SPAdminBotBeta?s=onFqEMZTaC4.cwA.Cwo.jTm_RSmb0Svg-areEJIwczJ3zwnFF1Bj64ccYtJEcT4
https://webchat.botframework.com/embed/hipstercatbot?s=dNn17GME34k.cwA.Q2M.PngrX97_gN0-KZIvTUYnfqDTIYA6SjuaAt4qvIiSnGM
[Note- All webchat bots are Vulnerable]
Impact
- Client-side attacks: Uploading malicious files can make the website vulnerable to client-side attacks such as XSS or HTML Injection, etc which can redirect users to a phishing website.
- Trust Breach: The attacker can use the upload functionality to upload malware which he/she can use to store or transmit to the victim for malware attack. The trust of the user on Microsoft is impacted as the malware is transmitted via Microsoft related domain.
Instance 1: Client-side attacks-Reflected XSS
Severity: High
CVSS Score: 7.1
CVSS Vector: AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:H/A:N/E:H/RL:O/RC:C/CR:X/IR:M/AR:X/MAV:X/MAC:X/MPR:X/MUI:X/MS:X/MC:X/MI:X/MA:X
Proof of Concept:
Step 1: Create a SVG(Scalable Vector Graphics) file with malicious javascript as shown below in Exhibit-1.1.1.
Step 2: Navigate to https://webchat.botframework.com/embed/TaxiLimeBot?s=xMHlV-9UR7c.cwA._H8.kLpVmFx6sOsqfBAKTic2_YqvcPsy5N8XBXT5a4h4jio
Step 3: Upload the created ‘kiwi.svg’ on the webchat. Observe that the file is uploaded successfully.
Step 4: Click on the uploaded file to get the link of the attachment
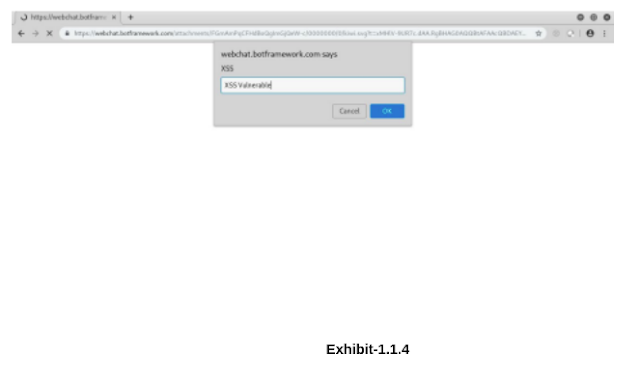
Step 5: Open the link in another browser(Here- Google chrome) and observe that the browser will give the pop up. The link can be shared/used to trick users to redirect to some phishing pages.
Expected Result:
The bot frame should not allow or block the harmful extensions like svg file to be uploaded.
Observed Result:
The attacker has uploaded the svg file and the link can be shared/used to trick users to redirect to some phishing pages.
Instance 1: Client-side attacks-HTML Injection
Severity: Medium
CVSS Score: 4.1
CVSS Vector: AV:P/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N/E:H/RL:O/RC:C/CR:X/IR:M/AR:X/MAV:X/MAC:X/MPR:X/MUI:X/MS:X/MC:X/MI:X/MA:X
Proof of Concept:
Step 1: Start server(Here- ngrok used) to get a public domain.
Step 2: Create a HTML form which is submitting the form data to the above server.
Step 3: Navigate to the https://webchat.botframework.com/embed/SPAdminBotBeta?s=onFqEMZTaC4.cwA.Cwo.jTm_RSmb0Svg-areEJIwczJ3zwnFF1Bj64ccYtJEcT4
Step 4: Upload the created ‘Microsoft SSO.html’ on the webchat. Observe that the file is uploaded successfully.
Step 4: Click on the uploaded file to get the link of the attachment and open in the browser. Enter the credentials and submit the form.
Step 5: Observe that the user credentials are logged on my server. The link of the form can be shared/used to trick user to get his/her Microsoft login credentials. The user will submit credentials considering it as Microsoft related domain and hence genuine.
Expected Result:
The bot frame should not allow or block the harmful extensions like html file to be uploaded.
Observed Result:
The attacker has uploaded the html file which can be accessed only locally and the link can be used to trick users to redirect to some phishing pages.
Instance 2: Trust Breach- Mode for Malware Transmission
Severity: Low
CVSS Score: 3.8
CVSS Vector: AV:P/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N/E:U/RL:O/RC:C/CR:X/IR:M/AR:X/MAV:X/MAC:X/MPR:X/MUI:X/MS:X/MC:X/MI:X/MA:X
Proof of Concept:
Step 1: Navigate to the https://webchat.botframework.com/embed/hipstercatbot?s=dNn17GME34k.cwA.Q2M.PngrX97_gN0-KZIvTUYnfqDTIYA6SjuaAt4qvIiSnGM
Step 2: Upload the Test_Malware.exe and observe that the file is uploaded successfully. The uploaded file is having a link now which can be shared/used for malware attack.
Expected Result:
The bot frame should not allow or block the harmful extensions like exe file to be uploaded.
Observed Result:
The attacker has uploaded the exe file which can be accessed locally and the link can be used to trick users to perform malicious activity.
Note- HTML Injection and Mode for Malware Transmission are possible only when attacker has the physical access of the user. The impact of both is very less, but it is an issue. These points should also be considered for patch subject to priority of Microsoft.