The security issue allows a malicious actor to bypass the naive security implementation of rate limiters. This allows an attacker to abuse the functionality of profile view count and increases them indefinitely. The following are the steps to reproduce wherein I have used my own blogger account
(https://www.blogger.com/profile/09844396241453600561)
Acknowledgment: Google Honourable Mentions (https://bughunter.withgoogle.com/rank/hm/9)
Steps to reproduce:
Implementation of Request Limiters
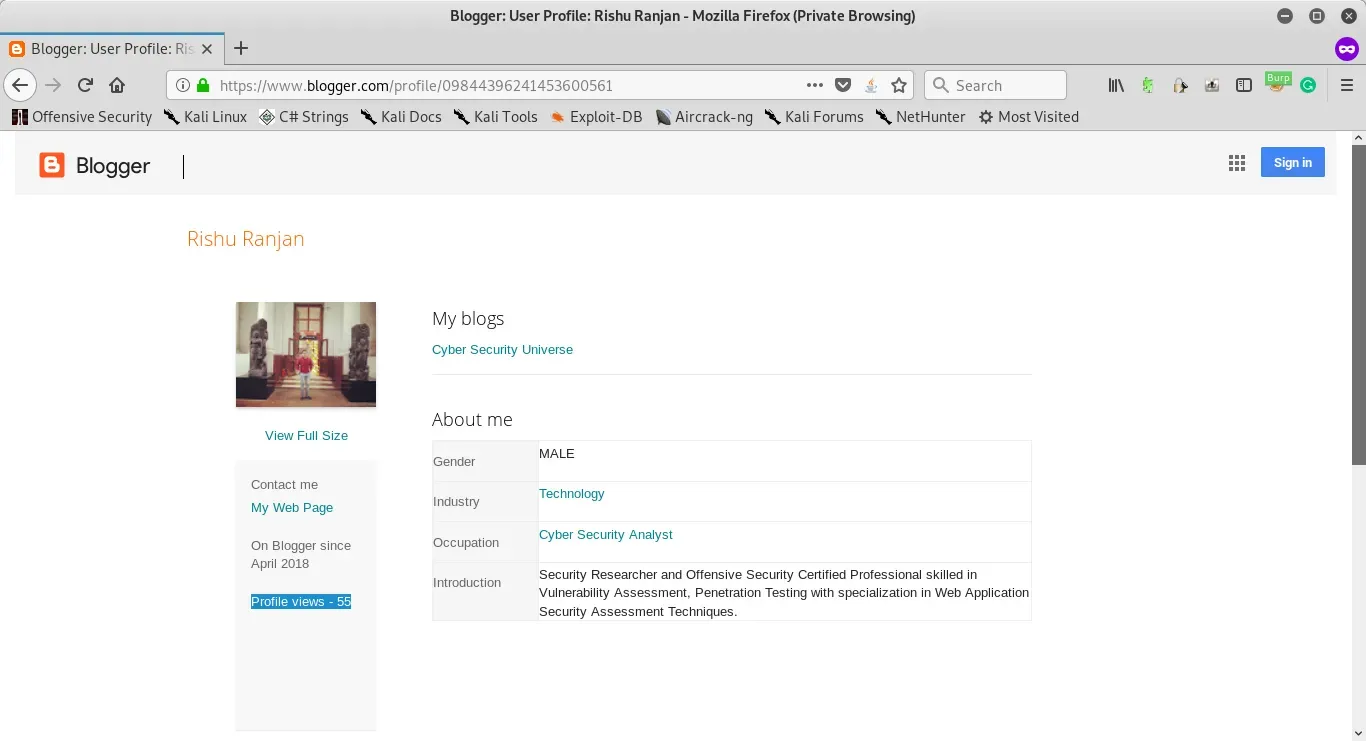
1. Open blogger profile(above mentioned URL) and note the profile view count as shown in Exhibit-1.
2. Capture the request in a proxy server such as Burp suite.
3. Send the captured request to Burp intruder as shown in Exhibit-2 and set the payload(null) to 1000 which will send 1000 requests to the server (Exhibit-3).
4. As shown by Exhibit-4 the naive security implementation blocks the automation attack after 300 requests, by implementing the Google CAPTCHA to redirect the request to the CAPTCHA request.
Bypassing Implemented Request Limiters
5. To bypass the security implementation, send the blocks of requests PARALLELY to the server with each block containing 299 requests as shown in Exhibit-5.
6. As shown by Exhibit-6 the naive security implementation is bypassed and the profile count is increased accordingly.
Attack Scenario:
Blogger user can increase the Profile view count for any user for his benefit or hamper any other user reputation. All blogger users profile URL is assessed and iterated without any login.